How To Report That You Verizon Phone Has Been Hacked

Baronial three, 2022
Telephone hacking occurs when a cybercriminal uses malicious software to infect and compromise vulnerable smartphones, stealing the personal data stored on those devices. Sure, smartphones tin can glitch from fourth dimension to time — no device is perfect. But how do you know when it's a simple hiccup or something a bit more serious?
That's where learning how to know if your telephone is hacked comes into play. And luckily for you, we have the answers. Use this guide to learn about telephone hackers, signs of a hacked phone, and how to help keep your phone safe. Yous won't regret making an effort to larn how to better protect one of your most used devices.
5 alert signs of phone hacking
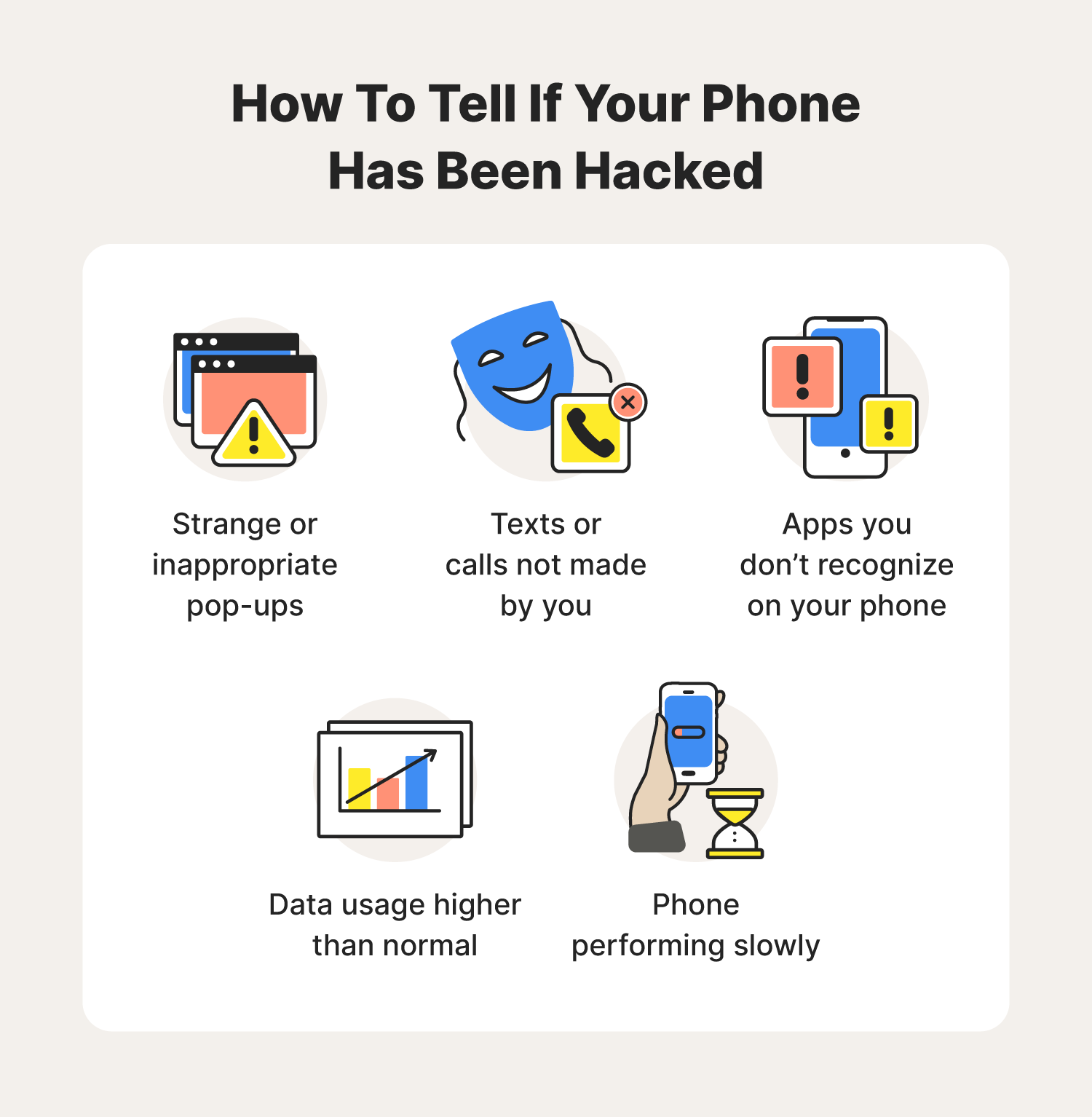
If your phone is displaying one of the post-obit unusual behaviors, and peculiarly if it'due south displaying more than one, there's a adept chance that it may be hacked.
i. Strange or inappropriate pop-ups:
One apparent sign of a hacked phone is nonstop popular-ups. Bright, flashing ads or X-rated content popping up on your telephone is a big indicator that your phone has been compromised.
ii. Texts or calls not fabricated by you
As the owner of your device, you likely recollect every fourth dimension y'all use your phone throughout the day. So, if you notice texts or calls from your phone that you didn't brand, you may have had your phone hacked.
iii. Higher than normal data usage
There are many reasons for high data usage (for example, increased use of a new app). But if your telephone behavior has stayed the same and your information usage has skyrocketed, information technology'south time to investigate.
4. Apps you don't recognize on your phone
Go on in mind that new phones often come with pre-downloaded apps. But if you lot notice new apps popping up once you already ain the telephone, there may be malware involved.
5. Bombardment draining quickly
Telephone batteries aren't meant to last forever, but they're also designed efficiently. And so, if your phone use habits have remained the same, but your battery is draining more than apace than normal, hacking may be to blame.
How to stop someone from hacking your telephone
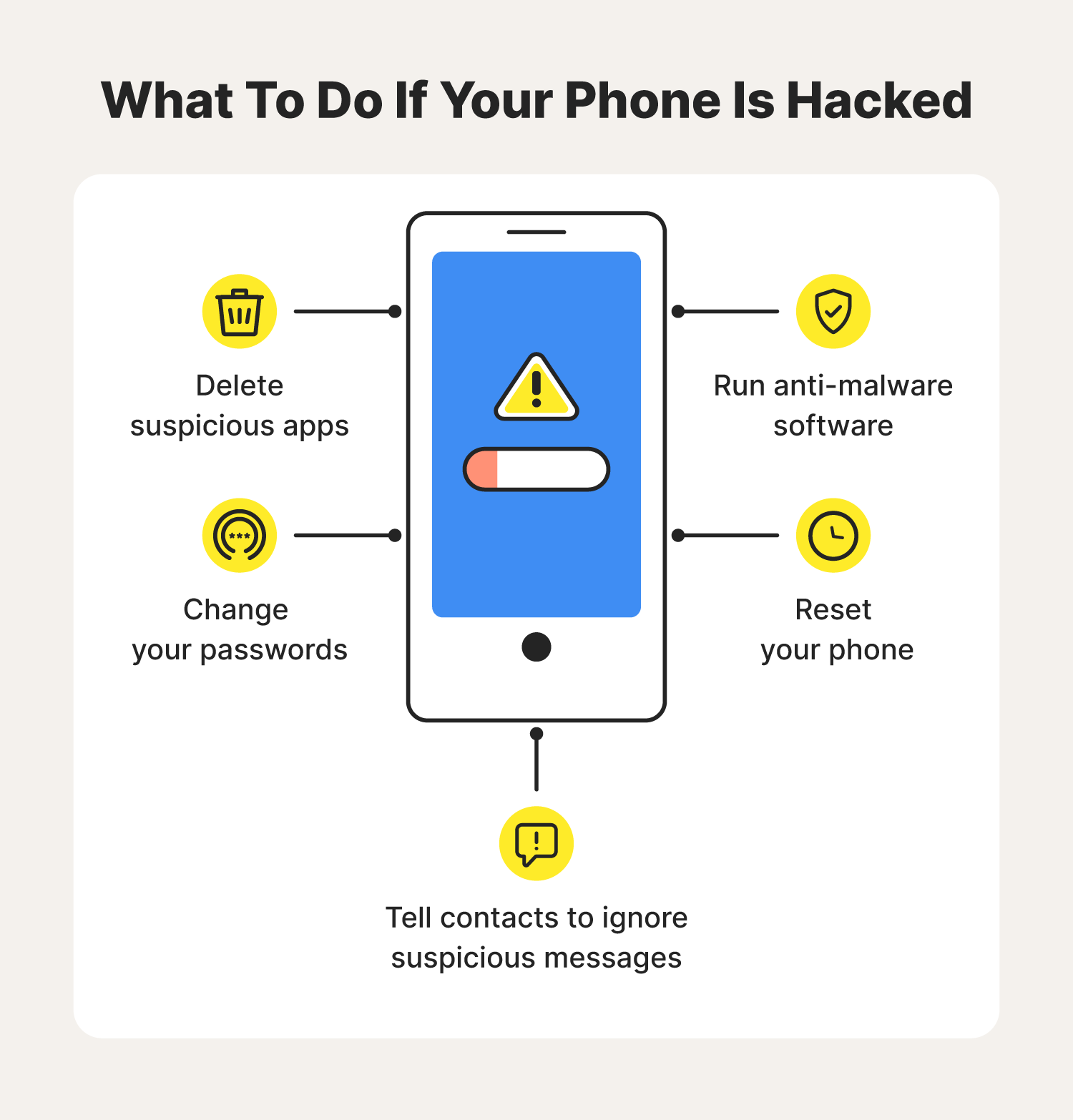
If you've determined that you're dealing with a compromised phone, there are some steps you tin have to address it. Before you start, we recommend letting your contacts know that your phone has been hacked, and that they shouldn't click any suspicious-looking links they may have received from you. Hither are more steps you lot can take.
Delete suspicious apps
Downloading a suspicious app is a common manner to invite malware onto your phone. If you find that your phone has been hacked, take an inventory of your apps and delete annihilation that came from a tertiary-party source (in other words, not the Apple App Store or the Google Play Store). Confirm that whatever recently downloaded apps came from reputable developers and have expert reviews. If they don't, delete them from your phone.
Run anti-malware software
Anti-malware software can help you lot identify and target malware lurking on your phone. Y'all should run this regularly, but if yous haven't done so before, now is a expert fourth dimension to showtime. If you're concerned about malware, information technology'south smart to consider trusted security software like Norton 360 Deluxe to help protect your devices and online privacy.
Reset your phone
The majority of malware tin can be removed with a manufactory reset of your phone. This will, however, wipe any data stored on your device, such as photos, notes, and contacts, then information technology's important to back up this information before resetting your device. Follow the instructions below to reset your iPhone or Android.
Instructions for resetting an iPhone
- If you lot have a Mac with macOS Catalina x.fifteen, open Finder. Otherwise, open iTunes.
- Connect your iPhone to your calculator.
- Select your device on your computer.
- Select "Restore iPhone."
For more detailed instructions, visit Apple tree back up.
Instructions for resetting an Android telephone
- Android reset instructions vary by manufacturer. You should visit your phone manufacturer's website for specific instructions.
- For nearly Android phones, y'all tin access the reset pick via your Settings carte du jour, or by belongings down the power and volume buttons.
For more than detailed instructions, visit Google support.
Change your passwords
Information technology's possible that your login credentials were compromised when your phone was hacked. Once you lot've removed the malware, reset all of your passwords and create unique passwords for each account.
five+ ways to avert phone hackers
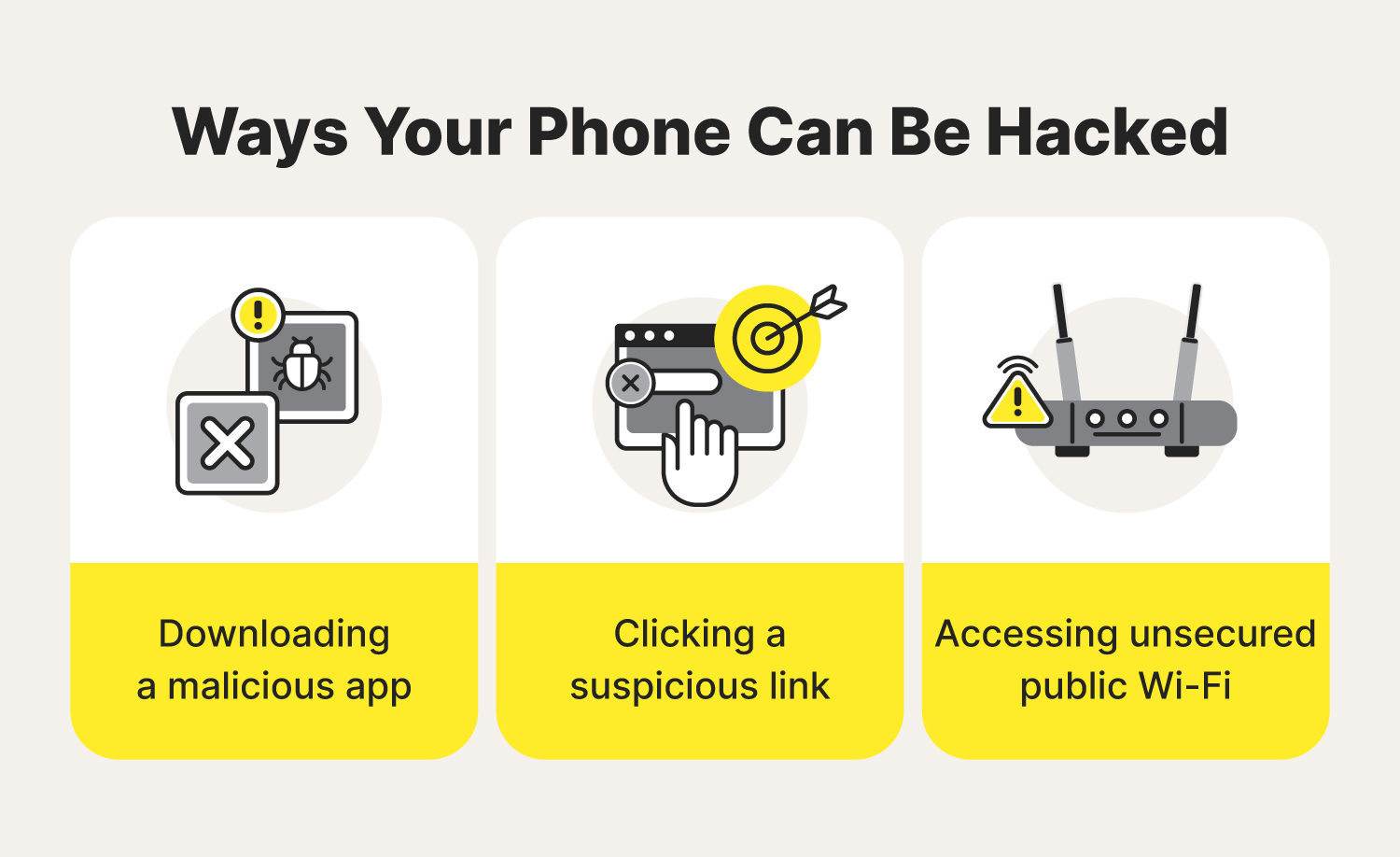
Nosotros've already discussed some of the ways you might unintentionally download malware on your phone, so assistance avoid that by diligently vetting apps, checking suspicious links before clicking them, and steering clear of public Wi-Fi.
Here are some more means you lot can keep your telephone secure:
- Avoid storing sensitive information (like credit card numbers) on your phone. Or, store them in a secure app.
- Turn off Bluetooth when you lot're not using it.
- Create a custom passcode for accessing your phone.
- Install the latest software updates every bit soon as they're released.
- Lock sensitive apps.
- Regularly monitor your phone for signs of unusual action, like pop-ups or loftier bombardment usage.
The prospect of a hacked phone is certainly scary, only the good news is that you tin can take steps to help forbid phone hacking (or to address information technology, if it'south already happened). Avert different mobile security threats by frequently monitoring your phone activity and being smart about what you click, download, and store.
Phone hacking FAQs
Accept questions beyond how to know if your phone is hacked? We have answers.
How do phones become hacked?
Smartphone hackers employ a variety of methods to compromise cell phones. These include:
- Phishing attacks
- Smishing attacks
- Spyware
- Scareware
- Unsecure Wi-Fi
- Malicious apps
Does resetting your telephone go rid of viruses?
Aye, a factory reset is one mode to potentially remove a virus from an infected mobile device.
Why practise hackers hack your phone?
Hackers compromise smartphones to access the personal information stored on each device, ofttimes exploiting and/or selling what they get their hands on.
Does turning off your phone stop hackers?
Aye, turning off your telephone can terminate hackers, as nigh cyberattacks targeting jail cell phones require the device to exist turned on.
Can hackers hear you?
Yes, hackers may be able to hear y'all if they've gained access to your phone's camera and microphone.
Does aeroplane mode block hackers?
Turning on airplane mode can temporarily cake hackers while the device is not connected to Wi-Fi or a cellular network.
What tin can a hacker exercise with your phone number?
Hackers often compromise phone numbers in order to:
- Verify 2FA requests
- Transport malicious links
- Complete vishing attacks
Tin can someone hack your phone and plough on your camera?
Yep, cybercriminals can hack phones to proceeds access to their cameras.

Norton™ 360 for Mobile
Powerful protection for your mobile device and online privacy – plus Dark Web Monitoring Powered by LifeLock™.
It's more important than ever to brand sure your mobile devices are secure and your personal information stays private. Norton 360 for Mobile helps deliver powerful, proactive protection for your device and personal information against stealthy cyberthreats and online scams.

Editorial note: Our articles provide educational information for you. NortonLifeLock offerings may non cover or protect against every type of offense, fraud, or threat we write about. Our goal is to increase awareness nearly cyber safety. Please review complete Terms during enrollment or setup. Recollect that no 1 can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses.
Copyright © 2022 NortonLifeLock Inc. All rights reserved. NortonLifeLock, the NortonLifeLock Logo, the Checkmark Logo, Norton, LifeLock, and the LockMan Logo are trademarks or registered trademarks of NortonLifeLock Inc. or its affiliates in the United states and other countries. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Shop is a service marking of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.Southward. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Artistic Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.
How To Report That You Verizon Phone Has Been Hacked,
Source: https://us.norton.com/blog/malware/is-my-phone-hacked
Posted by: dorseydouncestably.blogspot.com


0 Response to "How To Report That You Verizon Phone Has Been Hacked"
Post a Comment